January 3, 2024
Google is big. Google Search generated $225 billion in revenue in 2022, thanks in part to being the default search engine on all Apple devices. To retain that position—and continue to reap the ad revenue that it generates—Google pays Apple about $18 billion every year. Along with Apple, Google pays billions to phone manufacturers like Samsung, LG, and Motorola; major wireless carriers such as AT&T, T-Mobile, and Verizon; and browser developers like Mozilla and Opera.
So is Google Search’s 90% market share because it’s the best search engine or because Google has enough money to pay distributors for top placement?
Along with concerns about whether Google is the best search engine, some people worry about Google collecting information about them to show targeted ads alongside search results. The more information Google has on users, the argument goes, the better that ads can be targeted, and the more likely it is that users will click the ads, which generates money for Google from advertisers. Others worry that Google’s results may reflect certain types of bias.
If you’re perturbed by the privacy implications of Google knowing everything you search for, or if you’ve found Google’s search results less helpful than you’d like, you can easily switch to another search engine to see if you prefer its results and privacy stance.
How to Switch Search Engines
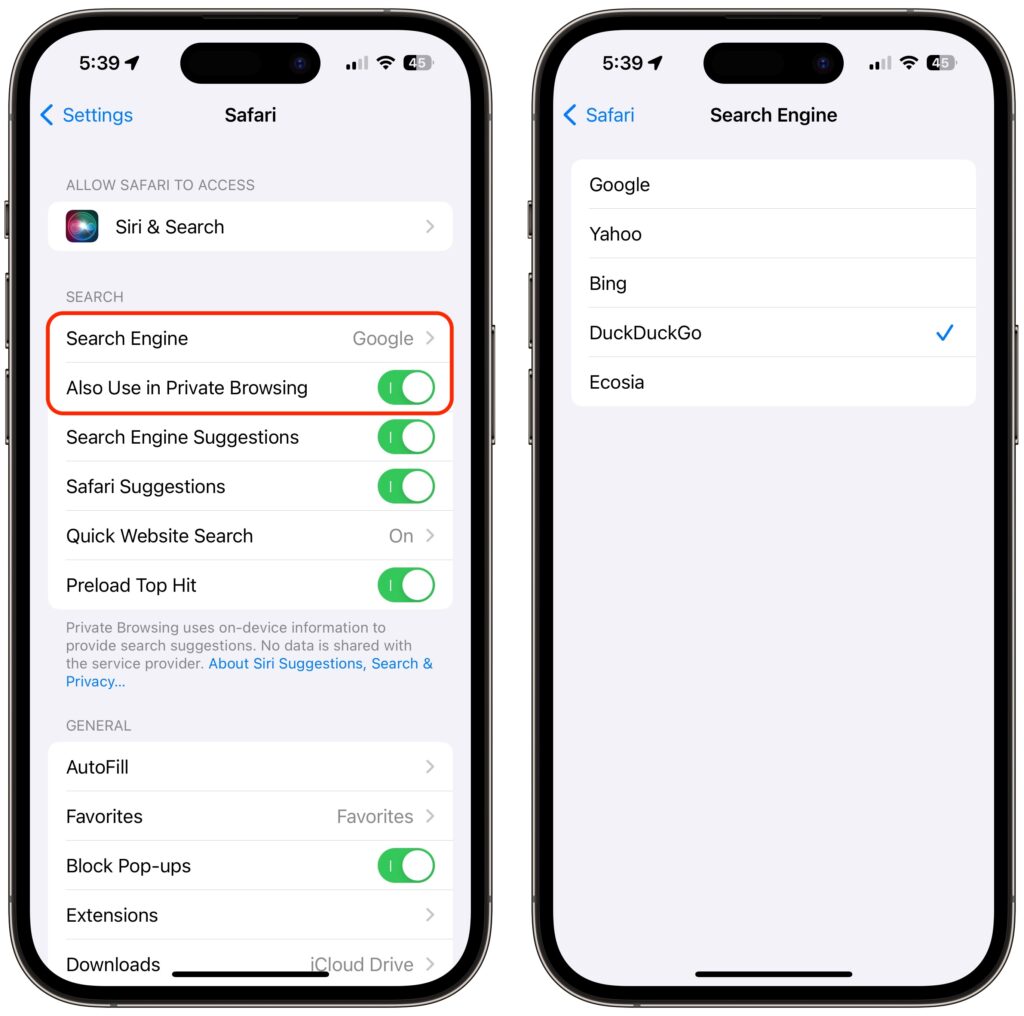
For many Apple users, the main place to choose a preferred search engine is in Safari’s settings. On the Mac, choose Safari > Settings > Search and choose the desired search engine from the Search Engine pop-up menu. You can choose a different one for Private Browsing windows if you want.
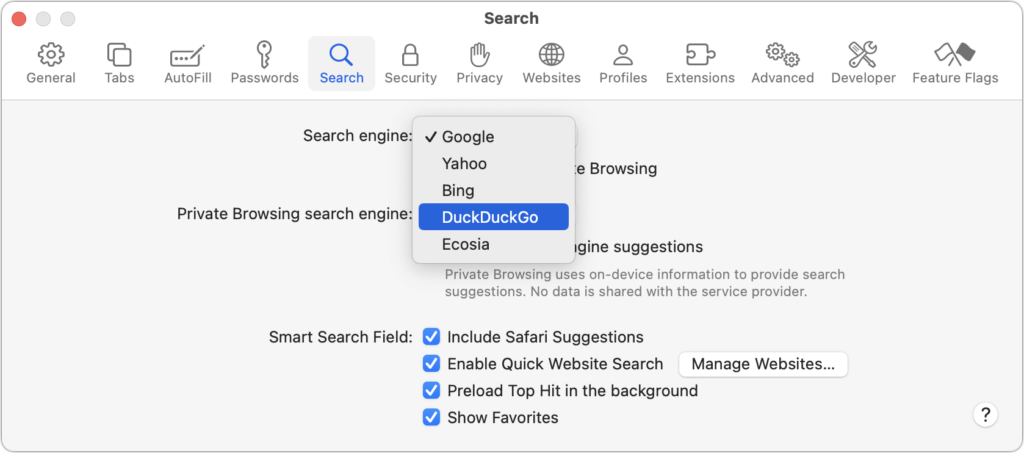
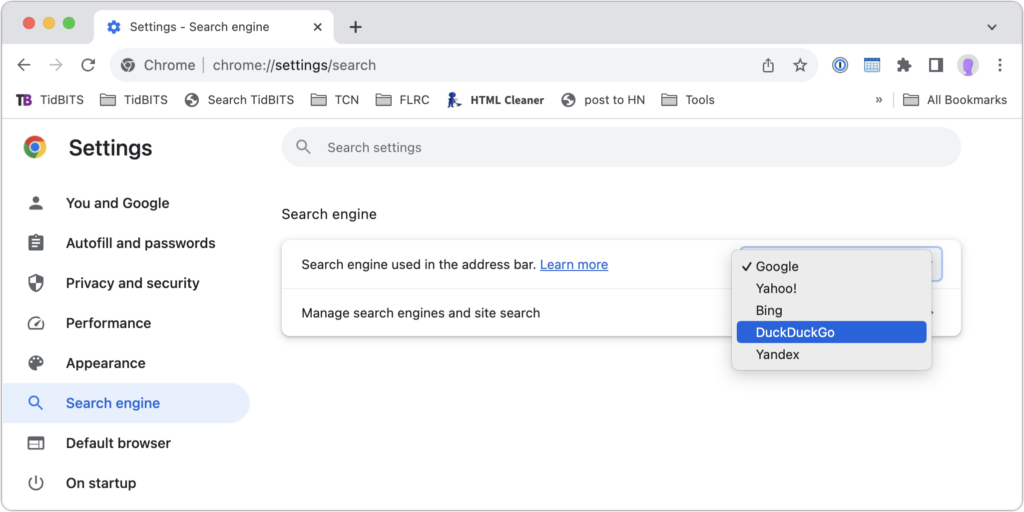
In Chrome-based browsers like Google Chrome, Arc, Brave, Microsoft Edge, and Opera on the Mac, open the settings and look for Search Engine. A pop-up menu lets you choose from some standard options, and additional choices let you add search engines like Brave Search that are too new (or not paying) to appear. Firefox offers similar options when you choose Firefox > Settings > Search.
On the iPhone and iPad, go to Settings > Safari > Search Engine. Again, if you want a different search engine in Private Browsing tabs, turn off Also Use in Private Browsing and choose another option.
Top Alternative Search Engines
Conceptually, what search engines do is simple—they search a set of Web pages for matching keywords and return a list of them in order of relevance to the user. The hard part is dealing with the number of pages—estimates suggest Google indexes 50 billion pages and Bing 4.5 billion—and scaling the service to respond instantly to tens or hundreds of millions of queries per day. (Google processes 8.5 billion searches per day; Bing handles 400 million.) Beyond Google, here are the main search engines and what sets them apart. (You will also likely see Yandex, sometimes called “the Google of Russia.” Avoid it. For so many reasons.)
- Bing: The second-most popular (though far, far behind Google) search engine in the world, Microsoft’s Bing sets itself apart with a busy, highly designed search results page that mixes a variety of results. It may work well for you, or you may find it overwhelming and difficult to parse. Microsoft is also putting a lot of effort into chat-based AI-powered results. Bing claims to offer more user privacy than Google, but it’s still tracking users to target ads better. If Bing has better privacy than Google, it may mostly be due to not being part of the larger Google data-collection empire.
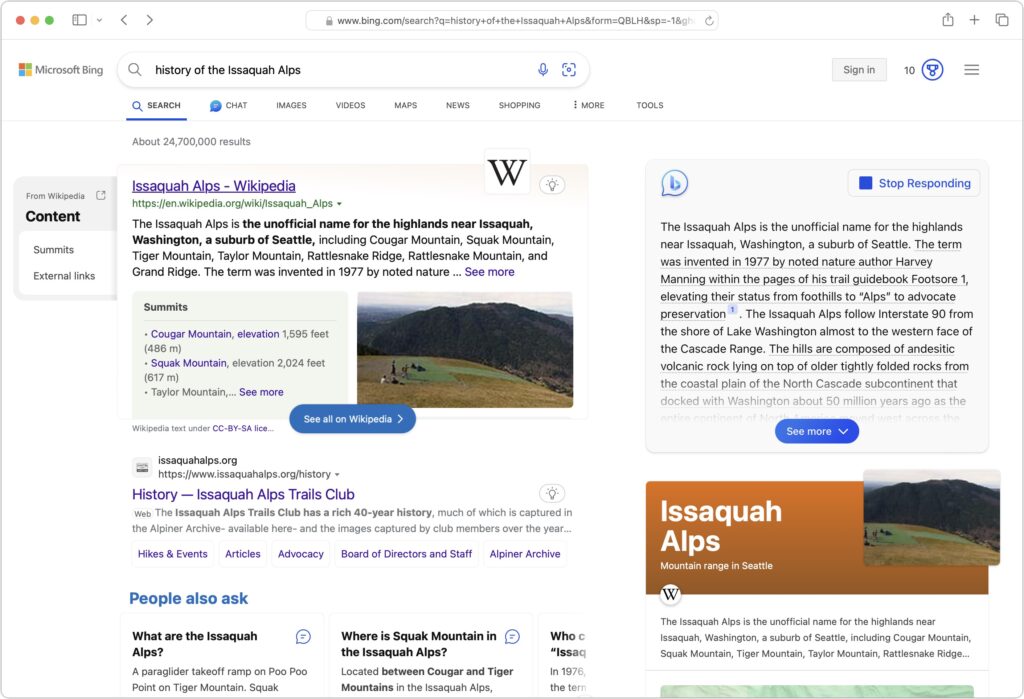
- Yahoo: Though it was the first Web search engine, Yahoo hasn’t run its own index since 2009. Today, Yahoo’s search results are powered by Microsoft Bing, so while the look of the search results page may differ, the results should be identical to Bing’s. Yahoo’s privacy stance is also similar to Bing’s.
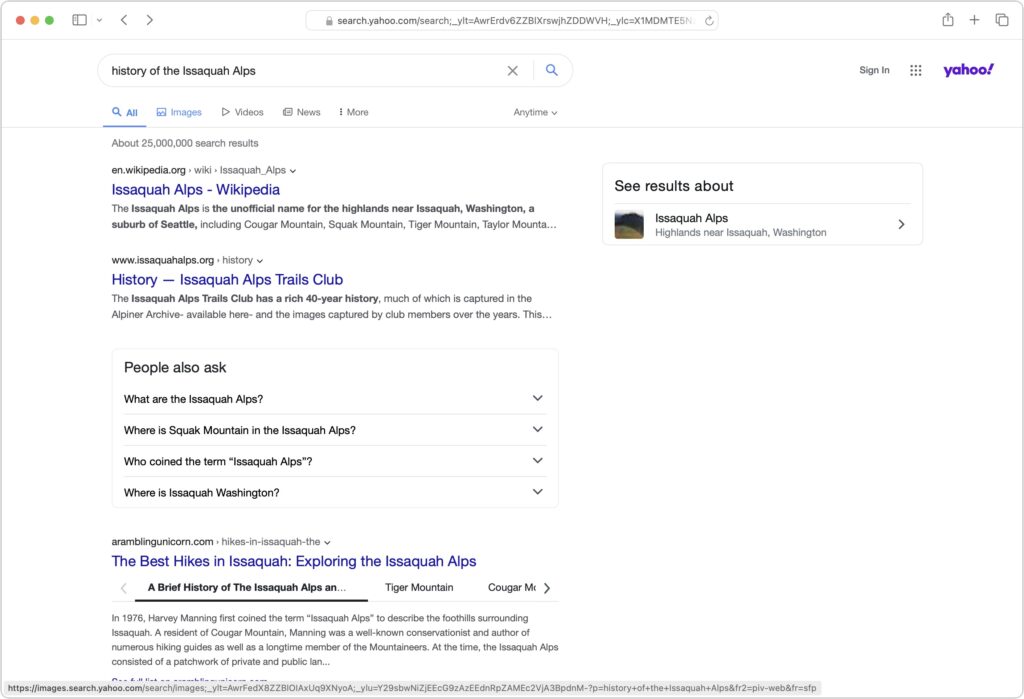
- DuckDuckGo: If privacy is paramount, DuckDuckGo is worth a look because it does not track or store user information at all. Instead, it chooses ads to display only by matching with search keywords. Although it uses Bing for some of its results, DuckDuckGo also incorporates information from numerous other sources, so it won’t seem like an exact clone of Bing.
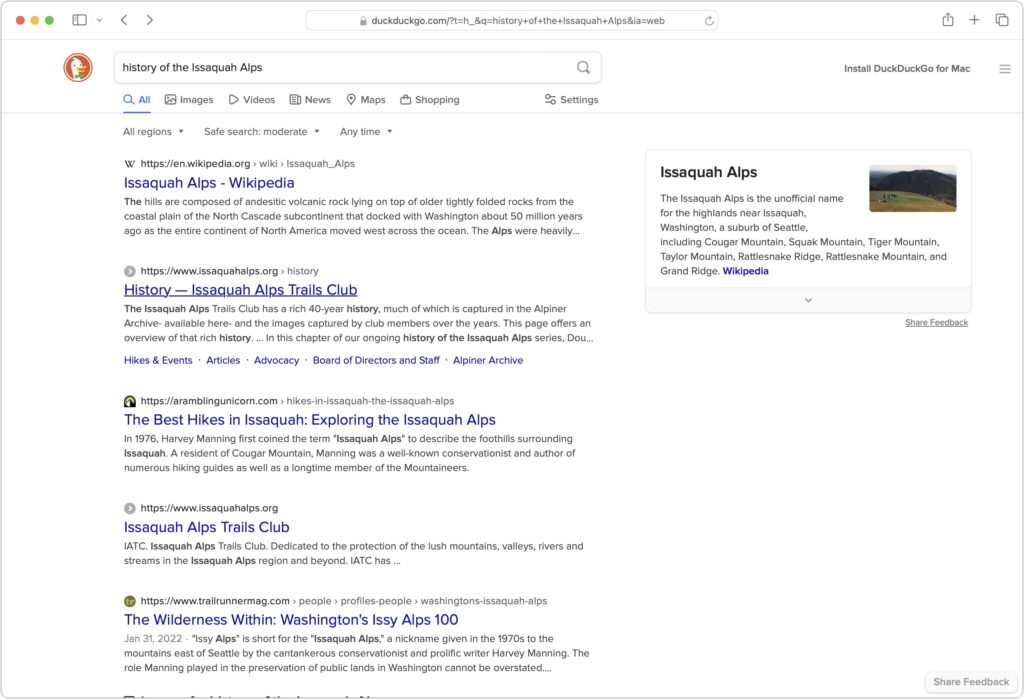
- Ecosia: The main reason to use the Berlin-based Ecosia is if you like Bing’s results (but not its layout) and want to support a “social business” that claims to be carbon-negative, offers full financial transparency, and protects users’ privacy. Founded in 2009, Ecosia today relies entirely on Bing’s search results and ads (clicks on which are how Ecosia earns money), and it claims to have planted over 188 million trees in 35 countries since its inception. It’s hard to argue with Ecosia’s environmental results, but as a search engine, it doesn’t feel special.
- Brave Search: A truly independent search engine, Brave Search relies on its own created-from-scratch index (it leaned on Google and Bing for some results early on, but ceased in August 2023). It also emphasizes user privacy and doesn’t track users, searches, or clicks. Although Brave Search displays keyword-based ads by default, users can pay $3 per month for Brave Search Premium, which provides ad-free results pages. You’ll have to set Brave as the default search engine for most browsers manually; for Safari, all you can do is make a favorite to search.brave.com.
- Kagi: Speaking of paid search engines, if you really want to avoid ads, Kagi is another independent search engine that rolls its own index and provides access only to subscribers, eschewing ads entirely. You can sign up for a 100-search test account, and if you like it, pay $5 per month for 300 searches or $10 per month for unlimited searches. As with Brave Search, you must manually set Kagi as the default search engine (there’s an extension for Safari).
The “best” search engine is the one that gives you the answers you want without triggering privacy worries or concerns about bias. If you want to see if something other than Google will work better for you, set it as your default search engine and try it for a few weeks.
(Featured image by iStock.com/Prykhodov)
Social Media: Have you become disillusioned by Google due to its search quality or how it tracks your activity to serve targeted ads? You can try other search engines that promise to protect your privacy and provide independent search results.